Tackling Shadow IT: How Microsoft Defender for Cloud Apps and CASB Can Help
In today’s fast-paced digital environment, employees often turn to unauthorized applications and services commonly referred to as Shadow IT to meet their immediate needs. For Example, instead of using OneDrive for Business which is your companies approved file share with controls on how the data is accessed and shared, they will instead go to WeTransfer, Dropbox, exfiltration of data via their personal Google Drive or OneDrive. It is likely within your business there are no controls to prohibit this behaviour. Again a user could sign up for an account on any app on any website without our express consent or knowledge. While these tools can enhance productivity and collaboration, they also pose significant security risks as they often operate outside the organization’s established security protocols. In this blog post, we’ll explore the challenges of Shadow IT and how Microsoft Defender for Cloud Apps, as a Cloud Access Security Broker (CASB), can help organizations gain visibility and control over their cloud usage.
Understanding Shadow IT
Shadow IT refers to the use of applications and services by employees without the explicit approval or knowledge of the IT department. This can include anything from cloud storage solutions to collaboration tools and productivity apps. While employees may adopt these tools to improve efficiency, Shadow IT can lead to several challenges, including:
Data Security Risks: Unauthorized applications may not comply with the organization’s security policies, increasing the risk of data breaches and leaks.
Compliance Issues: Using unapproved tools can result in non-compliance with industry regulations, exposing the organization to legal and financial penalties.
Lack of Visibility: IT departments often struggle to monitor and manage Shadow IT, making it difficult to assess the potential risks associated with these applications.
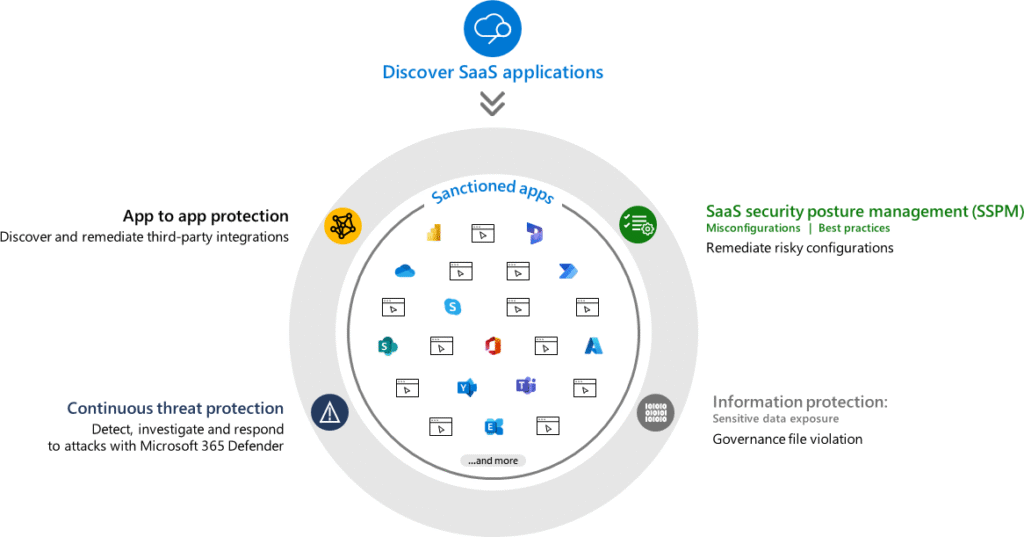
How Microsoft Defender for Cloud Apps Can Help
Microsoft Defender for Cloud Apps serves as a Cloud Access Security Broker (CASB), providing a comprehensive solution to help organizations manage and secure their cloud applications effectively. Here’s how it can address the challenges posed by Shadow IT:
Visibility into Cloud Usage: Defender for Cloud Apps provides organizations with deep visibility into all cloud applications being used within the organization. By analyzing traffic patterns and user behavior, IT teams can identify unauthorized applications and assess their risk levels.
Risk Assessment and Classification: The platform automatically classifies cloud applications based on their risk profiles, helping organizations understand which applications pose the greatest security threats. This classification is based on various factors, including compliance certifications, security features, and data handling practices.
Policy Enforcement: With Defender for Cloud Apps, organizations can create and enforce policies to manage Shadow IT effectively. For example, IT teams can set up alerts for risky behavior, such as accessing sensitive data from unapproved applications, and take appropriate action to mitigate risks.
Blocking File Uploads to Unknown Apps: One of the critical features of Defender for Cloud Apps is the ability to block file uploads to applications that are not recognized or approved by the organization. This capability is essential for preventing sensitive data from being inadvertently shared or stored in unauthorized applications, which can lead to data leaks and compliance issues. By implementing this control, organizations can maintain tighter security over their data and ensure that it is only stored in approved environments.
Integration with Existing Security Solutions: Microsoft Defender for Cloud Apps seamlessly integrates with other Microsoft security solutions, such as Microsoft 365 and Azure Active Directory. This integration allows organizations to leverage existing security investments and create a unified approach to cloud security.
User Education and Awareness: By providing insights into cloud usage and potential risks, Defender for Cloud Apps can help organizations educate employees about the importance of using approved applications. This awareness can foster a culture of security and encourage employees to seek IT approval before adopting new tools.
Conclusion
Shadow IT presents significant challenges for organizations, but with the right tools and strategies, these risks can be effectively managed. Microsoft Defender for Cloud Apps, as a Cloud Access Security Broker (CASB), offers a robust solution for gaining visibility and control over cloud usage, helping organizations identify unauthorized applications, assess their risks, and enforce security policies. By leveraging this powerful tool, businesses can enhance their security posture, ensure compliance, and empower employees to use technology safely and effectively. If you’re ready to tackle Shadow IT and strengthen your cloud security strategy, contact us today to learn how Microsoft Defender for Cloud Apps can help your organization thrive in the digital landscape.
